If you work in healthcare, whether you’re running a clinic, handling billing, or managing patient records, you’ve likely heard the term HIPAA more times than you can count. And for good reason: the Health Insurance Portability and Accountability Act (HIPAA) is what helps ensure patient information stays private, protected, and secure.
The original HIPAA rules from the early 2000s aren’t quite enough. Ransomware, phishing emails, and hacking incidents are now daily threats in the healthcare space, putting electronic protected health information (ePHI) at serious risk.
To respond to these growing threats, the U.S. HHS Department introduced an important update to the HIPAA Security Rule in January 2025. These changes are designed to bring cybersecurity practices up to modern standards and help healthcare providers and their partners build stronger defenses around sensitive patient data.
- According to the U.S. Department of Health and Human Services, the goal of HIPAA Security Rule 2025 update is to “strengthen the security of electronic health information while offering flexibility for organizations of all sizes.
So whether you’re part of a large hospital or a small private practice, understanding these updates is key to staying ahead of potential risks, and out of regulatory trouble.
Let’s break it down together.
The Urgent Need Behind the 2025 HIPAA Cybersecurity Update
According to the Office for Civil Rights (OCR), healthcare data breaches affected over 100 million individuals in 2023 alone, a record-breaking year for exposed patient data. And it’s not just about data being stolen. In many cases, cybercriminals are locking systems, demanding ransom payments, and bringing operations to a standstill.
- Ransomware attacks, where hackers freeze access to patient records and demand payment, have doubled in frequency since 2021.
- The average cost of a healthcare data breach now exceeds $10 million, according to IBM’s 2023 cost of a data breach report.
- Even email phishing scams have evolved, tricking staff into clicking malicious links that open the door to an entire network.
These threats aren’t just financial, they’re personal. Delayed surgeries, cancelled appointments, compromised mental health records – real people are feeling the fallout.
The new HIPAA Security Rule is meant to be a wake-up call and a roadmap. It acknowledges the realities of today’s digital threats and offers healthcare providers a more solid foundation to build a secure environment for patient care.
Whether you’re handling lab results, mental health notes, or insurance claims, protecting ePHI isn’t just a regulatory checkbox anymore – it’s a responsibility that impacts trust, safety, and care outcomes.
What’s New in the 2025 HIPAA Security Rule?
The new update in HIPAA Security Rule is designed to make protecting patient data more consistent, proactive, and realistic, even for small clinics and independent providers. Think of it like upgrading the locks, alarms, and emergency plans in your digital “clinic” – except the clinic is your EHR system, your emails, your cloud storage, and anywhere else ePHI (electronic protected health information) lives.
Minimum Cybersecurity Requirements for All Covered Entities
The new HIPAA Security Rule now establishes baseline cybersecurity standards that every organization must meet, regardless of size or complexity. These standards are intended to close the gaps that leave smaller healthcare practices vulnerable to data breaches. Key measures include:
- Secure user authentication
- Regular software updates and patch management
- Anti-malware solutions
- Employee training on cybersecurity awareness
This is especially relevant for practices managing patient data through platforms like HighLevel. With growing concerns around healthcare data privacy, ensuring system-level safeguards and user permissions are configured properly is now a compliance necessity.
Enhanced Risk Assessment and Documentation
Previously, many organizations treated risk assessments as a one-time event. Under the 2025 HIPAA rule, risk analysis must be ongoing, documented, and actionable. This means:
- Reviewing how ePHI is collected, accessed, stored, and transmitted
- Identifying new threats and vulnerabilities
- Creating formal records of mitigation efforts
HIPAA IT compliance requirements now demand more structured and recurring risk management practices, particularly for organizations using cloud-based EHRs and communication tools.
Mandatory Multi-Factor Authentication (MFA)
The new rule mandates multi-factor authentication (MFA) for remote access to systems containing ePHI. This significantly reduces the risk of unauthorized access, even if a password is compromised. Providers using digital tools like HighLevel must ensure:
- MFA is enabled across staff logins
- Authentication methods meet industry standards
- Remote workflows are secured
HIPAA compliance with HighLevel will require MFA as a standard feature across user accounts managing or accessing sensitive data.
Stronger Incident Response Protocols
The 2025 HIPAA security rule proposal also emphasizes the importance of incident response, both in preparation and execution. Requirements include:
- A written incident response plan
- Defined roles and escalation procedures
- Timely breach detection and response
- Notification processes that meet federal guidelines
This aligns with the broader trend of turning HIPAA from a reactive framework into a proactive one, ready for real-world cyber events.
Updated Technical Safeguards for ePHI Protection
The HIPAA IT compliance requirements now call for specific and enforceable technical protections, including:
- End-to-end encryption of ePHI in transit and at rest
- Automatic session timeouts
- Real-time audit logging and monitoring
Platforms like HighLevel should be evaluated to ensure these protections are integrated, or supplementary tools should be implemented where gaps exist.
- In 2024, Kaiser Foundation Health Plan, Inc. experienced a breach that exposed over 13.4 million patient records due to key issues like the lack of multi-factor authentication and outdated risk assessments. These vulnerabilities are specifically addressed in the 2025 HIPAA update, which aims to prevent incidents like this. Meeting these new requirements isn’t just about ticking boxes—it’s about safeguarding people’s lives and preserving the trust they place in us.
-HIPAA Journal, 2025
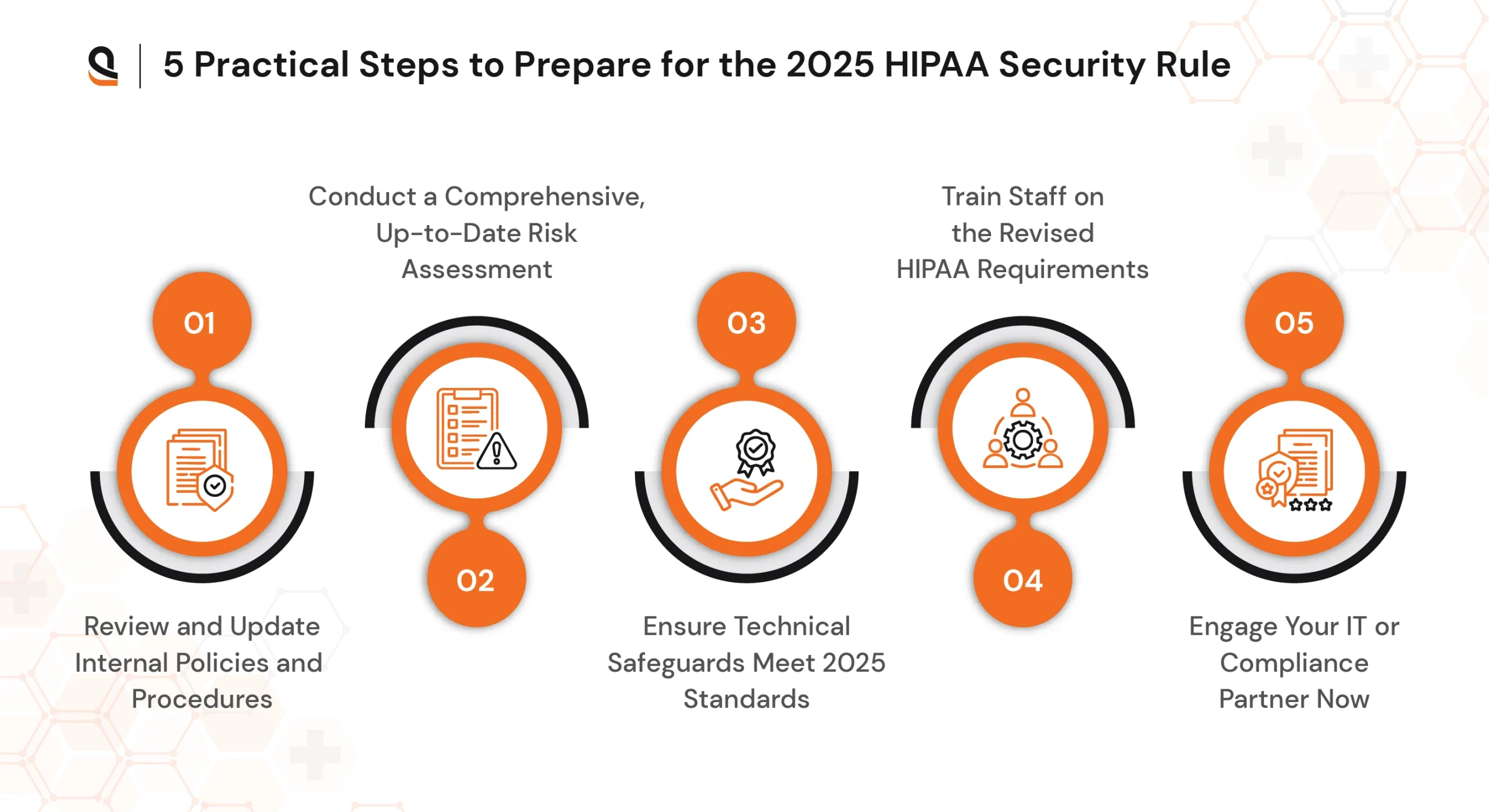
2025 HIPAA Security Rule: 5 Must-Do Steps for Healthcare Providers
The 2025 HIPAA Security Rule marks a significant advancement in healthcare cybersecurity expectations. While the updates may feel technical or regulatory in nature, their true purpose is to protect your patients, your data, and the continuity of your operations.
Whether you’re a multi-specialty practice, solo provider, or an IT partner supporting healthcare clients, here’s a breakdown of practical steps every organization should begin taking now to align with the new requirements and ensure full HIPAA compliance.
1. Review and Update Internal Policies and Procedures
Start with the foundation: your internal documentation. Existing policies should be thoroughly reviewed and updated to reflect the new standards introduced by the 2025 HIPAA Security Rule. Key focus areas:
- Data access controls
- Security incident handling procedures
- Remote work and mobile device policies
- Vendor management protocols
Your written procedures are the first thing an auditor or regulator will ask for in the event of a breach or investigation. Make sure they match how your team actually operates.
2. Conduct a Comprehensive, Up-to-Date Risk Assessment
HIPAA now emphasizes ongoing and documented risk analysis as a cornerstone of compliance. This is not a checkbox exercise, it should identify where ePHI is vulnerable and what controls are (or aren’t) in place. What to include:
- Inventory of all systems handling ePHI (EHRs, CRMs like HighLevel, communication tools, etc.)
- Assessment of physical, administrative, and technical risks
- Evaluation of third-party services and vendors
Your risk assessment will help you prioritize improvements and document your good-faith effort to comply with the new rule.
3. Ensure Technical Safeguards Meet 2025 Standards
The 2025 HIPAA updates call for specific technical safeguards, not just general intentions. This includes encryption, MFA (multi-factor authentication), audit logging, and data integrity protections. Steps to take:
- Confirm that all platforms (including marketing tools like HighLevel) support encryption at rest and in transit
- Enable MFA on all systems accessing ePHI
- Implement access logs and review them regularly
- Set auto-timeouts and role-based access permissions
If a platform or system you use doesn’t support these requirements, it may be time to reconsider or enhance it with third-party tools.
4. Train Staff on the Revised HIPAA Requirements
Even the best technical controls can’t protect your organization from human error. HIPAA compliance requires ongoing workforce training, particularly as the threat landscape evolves. Include in your training:
- Overview of the 2025 HIPAA changes
- Phishing and social engineering awareness
- Secure handling of patient information (digital and verbal)
- Reporting suspicious behavior or security incidents
Make HIPAA training part of your onboarding and annual review process. Compliance is a culture, not a one-time event.
5. Engage Your IT or Compliance Partner Now
Most healthcare providers cannot and should not manage these updates alone. If you work with an internal IT team or an external security vendor, now is the time to align your strategy with the new HIPAA requirements. Key topics to address:
- Security gap assessments
- Implementation of required technical safeguards
- System upgrades or vendor transitions (if current tools don’t comply)
- Business Associate Agreements (BAAs) with all vendors handling ePHI
Your IT team isn’t just a vendor anymore, they’re your partner in maintaining regulatory and reputational security.
Achieving HIPAA Compliance in 2025 with AQe Digital
The 2025 HIPAA Security Rule introduces stricter HIPAA IT compliance requirements that healthcare organizations must meet to protect electronic protected health information (ePHI). At AQE Digital, we leverage our expertise in AI and machine learning to help healthcare providers seamlessly meet these new requirements and navigate the evolving regulatory landscape. Our support could be understood as follows:
- Advanced Data Protection: We integrate AI-driven security solutions to automate encryption, access control, and multi-factor authentication (MFA) to ensure HIPAA compliance with HighLevel and other platforms. Our systems provide real-time monitoring and predictive threat detection to keep your data secure.
- Efficient Risk Assessment: Our AI-powered risk analysis tools continuously evaluate your systems for vulnerabilities, helping you stay compliant with HIPAA’s risk management requirements and ensuring you’re always prepared for audits.
- Seamless Vendor Compliance: With our advanced compliance management tools, we ensure that all third-party vendors handling ePHI meet the latest HIPAA requirements, helping streamline Business Associate Agreements (BAAs) and minimize vendor-related risks.
- Automated Training and Awareness: We provide AI-based training solutions tailored to your staff’s needs, ensuring everyone remains up to date on HIPAA changes 2025 and maintains secure practices when handling ePHI.
- Incident Response and Reporting: In the event of a breach, our AI-enhanced incident response tools quickly detect, contain, and ensure timely breach reporting, making sure your organization meets HIPAA’s breach notification standards.
AQe Digital is all about making HIPAA compliance easy and efficient. Moreover, with our Digital Transformation in Healthcare services, we infuse AI and ML to bring innovation, security, and smarter workflows to your organization. Contact us today to learn how our solutions can help you stay ahead of the curve and protect your patients’ sensitive data.