Cyberattacks have increased their sophistication while data breaches occur on an unprecedented scale. According to Verizon’s 2023 Data Breach Investigations Report, 74% of data breaches result from human error or social engineering, revealing how web applications can become insecure without proper app security measures.
Web applications often handle sensitive information regarding their users, personal identification numbers, credit card information, or sometimes even their private messages. Theft and leaking of such data could cause troubles like identity theft, financial loss, and reputational damage. Weak authentication and authorization policies make applications open to unauthorized access and, thus, the dangers of data theft, identity theft, or malicious activity in other ways.
Strong authentication and authorization systems like OAuth and JWT cut out most of these threats. The integration of OAuth JSON Web Token solutions ensures secure access control while mitigating risks associated with unauthorized entry. Looking forward, we are automating the way these instruments, including JWT OAuth2, will shape the future of secure web ecosystems.
As such, websites usually deal with customer-sensitive data, be it personal information, credit card details, or even private messages. Theft or leakage of such data would cause personal identity theft, financial loss, and reputational damage due to rumors and significant economic barriers. An application that does not have decent authentication and authorization would be vulnerable to unauthorized entry into the application, which can lead to exposed data theft or immoral action.
The strongest type of authentication and authorization, like OAuth and JWT (JSON Web Tokens), actually applies in securing most of the threats. Let’s move to understanding how such tools are going to be instrumentalized in making secure web ecosystems in the future.
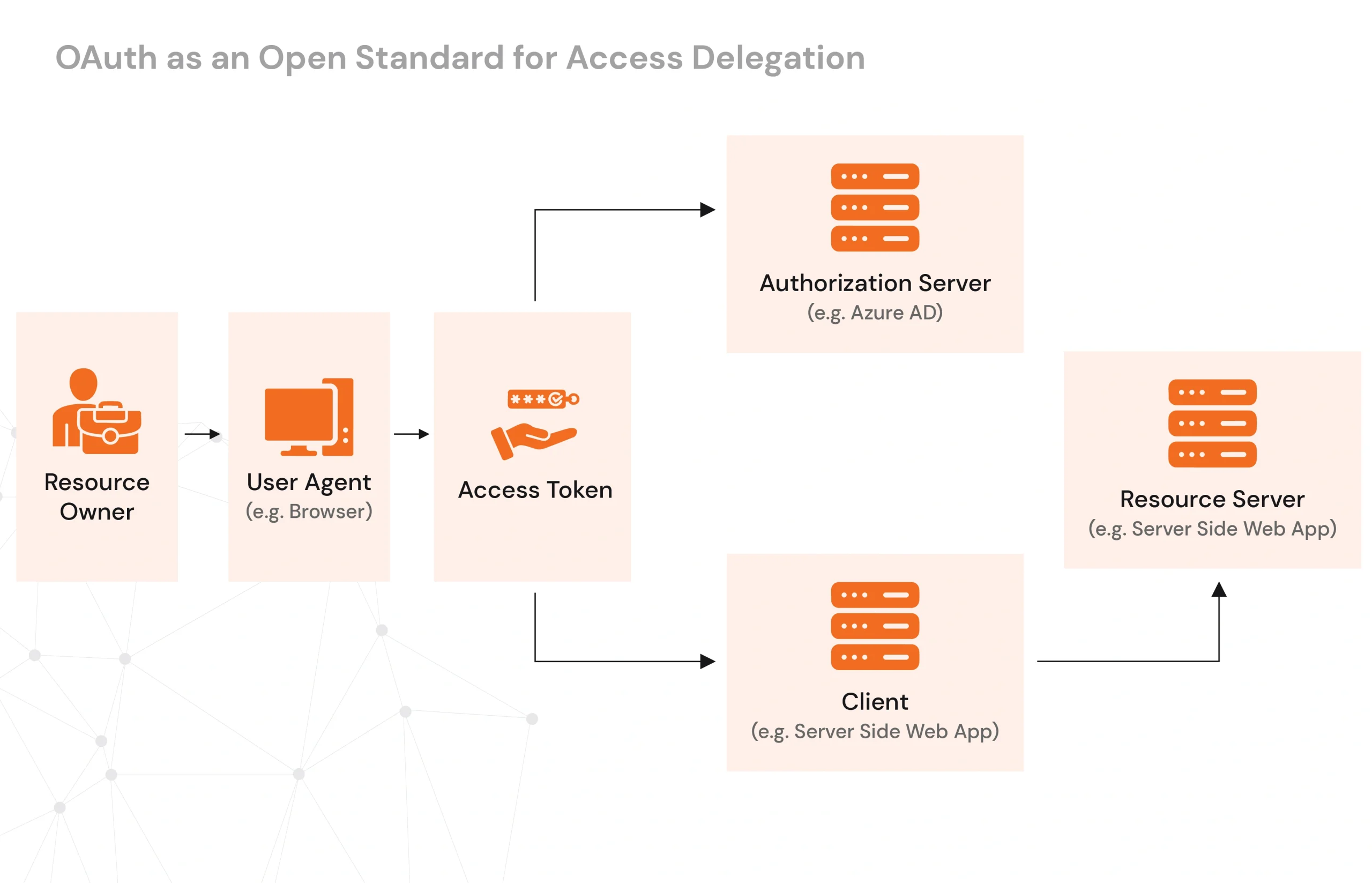
OAuth 2.0 as an Open Standard for Access Delegation
OAuth 2.0 (Open Authorization) is the most popular open standard allowing secure delegation access without revealing sensitive credentials to the user. Thereby, it allows the user to grant limited access to a resource, usually data or service, that can make use of an application’s third-party features without disclosing passwords or other sensitive information. OAuth 2.0, often implemented with JSON Web Tokens, is a widely used strategy in API development and integration for secure resource access.
Here is the best part of OAuth 2.0 security:
- OAuth 2.0 clearly separates the roles of the Resource Owner (the user), Authorization Server, Resource Server, and Client. This limits the amount of sensitive data that is exposed and credential vulnerability. With OAuth and JWT, secure authentication and authorization are achieved using tokens, reducing the risk of credential leaks.
- OAuth 2.0 granularity permission authorization. A user can give a particular third-party app the ability to access their Google Calendar without granting access to their inbox, for example. This is the principle of least privilege, whereby only those required permissions would be granted. OAuth with JWT further enhances this by enabling stateless authentication using JSON Web Tokens, ensuring efficient and secure access control.
- Tokens transfer via HTTPS to prevent unauthorized interception. Token-based authentication is the new OAuth 2.0 model and doesn’t require entry of sensitive user credentials as username and password. Using JWT OAuth2, the authentication process becomes even more secure as JSON Web Tokens allow for self-contained and verifiable claims.
- This fine-grained access control is possible with scopes that define permissions granted by the client while restricting access only to what it needs. OAuth JSON Web Token-based systems allow clients to request specific permissions, ensuring minimal access to user data.
- The state parameter allowed use with OAuth 2.0 to mitigate CSRF attacks and prevent any redirection attack ensured between client request and response. With OAuth and JWT, additional app security mechanisms can be implemented, making authentication processes even more resilient.
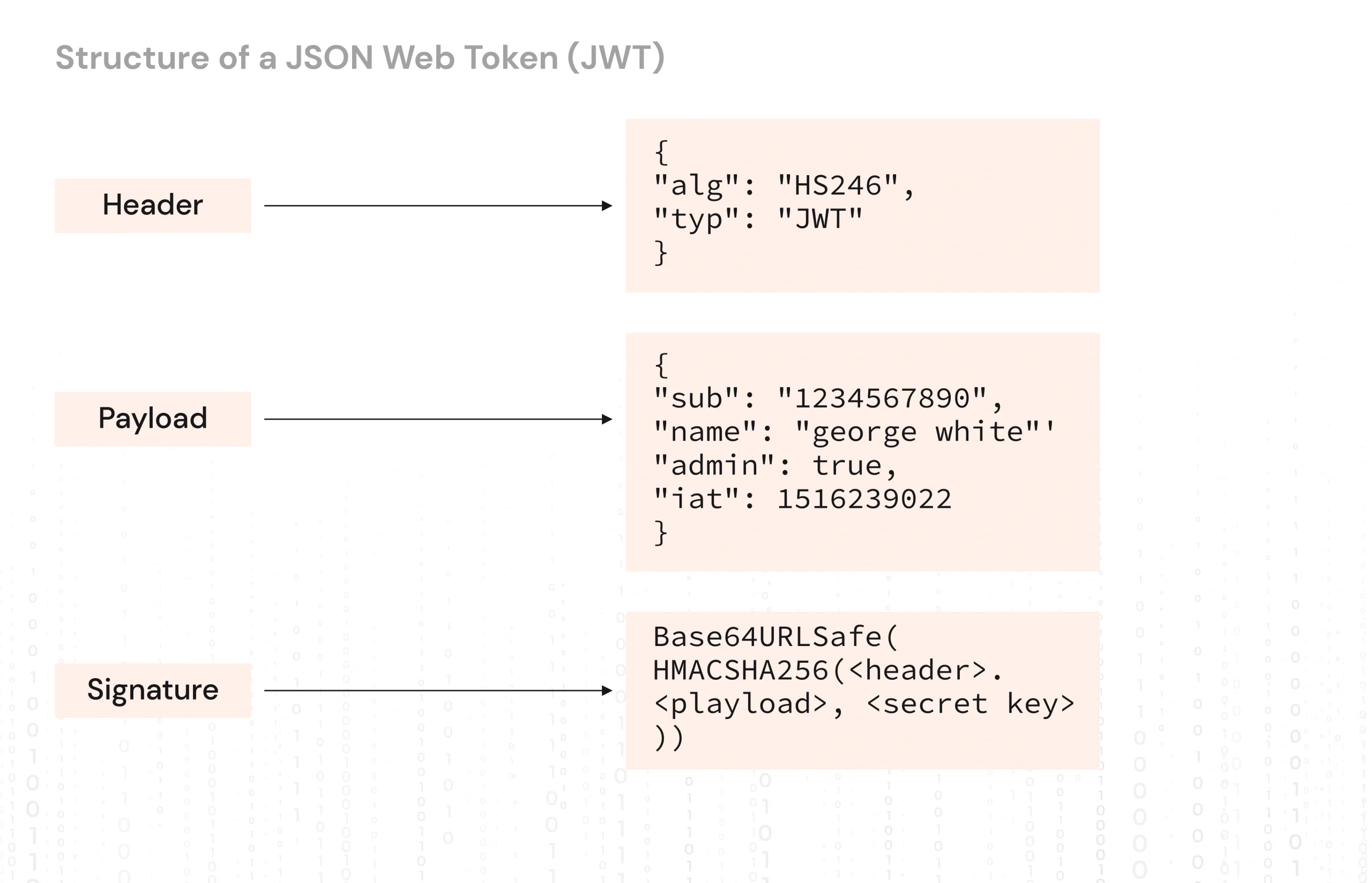
JWT as a Compact and Self-Contained Method for Transmitting Information
JSON Web Token (JWT) is an open standard widely adopted (RFC 7519; RFC 6749) that specifies an easy, safe means of presenting claims to be transferred between two parties.
JSON Web Token is composed of three parts—the header, the payload, and the signature—which ensure the data’s compactness, facilitate transmission, and safeguard it from being tampered with.
An intuitive yet robust mechanism for passing data in between a client and server, JWT has become a modern technology of choice for custom software solutions that require scalable and secure user authentication owing to its compact size, self-sufficiency, and ease of use. Along with identity, it should also specify the permissions (claims) assigned to the user in relation to certain inactivity. Such tokens can be sent from application to application or service to service, often as part of the HTTP request headers, for authentication authorization-brushing-in.
Some of the benefits of JWT include:
- JWTs are very lightweight for sending them around in HTTP headers, URL query parameters, or cookies. The compactness allows for easy transmission of a network to save bandwidth as well as speed up performance.
- As such, all the required information is in JWT (i.e., about the user and the expiry of the token). No centralized session store is in demand.
- The token contains all the necessary information, which allows servers not to keep session states across requests. This makes it the most effective token for scalable systems.
- JWT is a language-neutral identifier and can be used in any platform with JSON parsing. Therefore, it is widely adopted in different environments such as web applications and mobile applications.
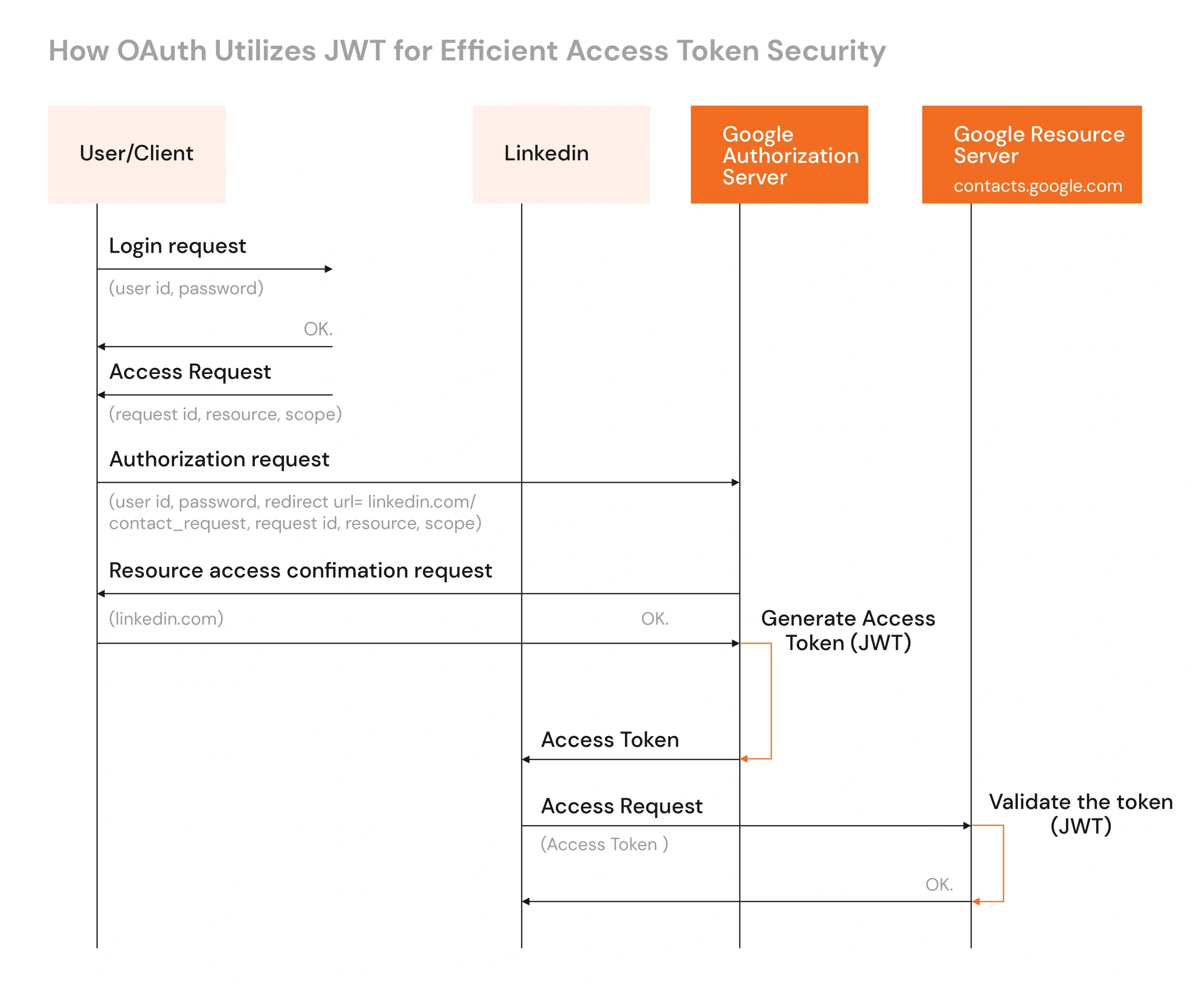
How OAuth 2.0 Utilizes JWT for Efficient Access Token Security
OAuth 2.0 and JWT (JSON Web Tokens) are a sturdy mixture of regulating authorizations and exchanging information in today’s style for web app security. OAuth 2.0 concerns itself with authorization so that users will be allowed to grant limited access to their resources without sharing their credentials, while JWT is the token that carries user claims and authorization details in a secure, compact, and self-contained way.
OAuth 2.0 does not require any particular format for an access token, while JSON Web Token has become the de facto standard due to its compactness and the means of securing claims in a self-containing manner.
This is how OAuth 2.0 uses JWT as an access token:
- Whenever a client application (such as a web or mobile app) seeks access to some protected resources (like user data on Google or Facebook), it redirects the user to the authorization server first (OAuth 2.0).
- Upon successfully authenticating and granting permission, the authorization server now gives the access token to the client.
- The access token is often a JWT. Using its private key, the authorization server signs the token, ensuring that it can be trusted and verified by other services that use the corresponding public key.
- The JWT access token contains various claims, which include:
- User identity (sub claim): The user that the access token was issued to.
- Expiration (exp claim): An expiration time for the current access token.
- Issued at (iat claim): The time at which the token was issued.
- Scope (scope claim): The permission or access levels that were granted to the client (for example, some permission such as to read or write).
- When the client sends a request to the resource server (to access user data or perform an action), it sends along the JWT access token in the HTTP request, usually in the Authorization header.
- The resource server checks that the token is authentic by validating the signature against the public key associated with the authorization server.
- Whenever the token is valid (not expired; signature matched), the server processes the request; in any other case, the request shall be forbidden with an error response.
- The self-contained nature of JWT means that the resource server does not consult any centralized session store or database for token validation. It can validate the token locally, thus facilitating extra scalability and less load on the server.
- On its end, this information is very important to taking care of distributed systems, especially when talking about microservices architecture, because no session data has to be stored on the server.
Effective Guidelines for Implementing OAuth 2.0 and JWT Authentication
When building web applications with OAuth 2.0 and integration of Json Web Token, one of the most sensible ways to follow best practices ensures app security and performance. Indeed, OAuth 2.0 and JWT can be very powerful and offer significant capabilities for authentication and authorization, but improper implementations are vulnerable. Here are some of the best practices in which modern web applications should pay attention to while dealing securely with OAuth 2.0 and JWT.
- Use HTTPS for all data transmission. This is to ensure that even during communication among different areas of your system, for example, between the server and a client, a user’s information is kept confidential.
- Encryption mechanisms should be strong for signing JWT tokens; this way only trusted parties can create or validate such tokens. Popular and secure methods include RS256 or ES256 algorithms.
- Limit the validity of access tokens, say 15-30 minutes. Use refresh tokens, so users don’t have to log in every time they want to access a service.
- Set scopes to limit what parts of the system an app can access. For example, don’t give an app that only needs reading user data rights to modify or delete it.
- Every time a token is used, you check its signature and make sure the token is still valid (not expired), for example, by checking the issuer and expiration date.
- Store refresh tokens securely, in either httpOnly cookies (which are harder for attackers to access) or secure storage. Rotate refresh tokens regularly so it becomes harder to exploit.
- In place of a token revocation mechanism. This will be helpful whenever a user logs out or when they decide to change their password.
- Never save sensitive information like passwords in a JWT. Only store user-related claims (e.g., user ID, roles, or permissions) to keep the system secured.
- Regularly rotate (change) app security keys that sign tokens. So that, if a key is compromised, it will not be usable for a long time. This keeps app security up high levels for a long time.
Role of AQe Digital in Securing Web Applications Using OAuth and JWT
As a reliable cloud security solution provider, we develop secure and highly scalable web applications with the core technology enablers being OAuth 2.0 implementation and JWT authentication. Our technical team understands that these technologies protect user data, and we mark our commitment to lay down app security best practices while building your web applications. Here’s how AQe Digital would help you secure your web application:
- OAuth 2.0 Implementation & Integration – AQe Digital specializes in seamless OAuth 2.0 integration so that data may be accessed securely by third-party apps without invading users’ privacy. The expert team comprehensively handles various OAuth 2.0 types like Google OAuth 2.0 and custom OAuth 2.0 and integrates it securely for a seamless user experience.
- JWT Authentication for Scalable Web Apps – Stateless yet secure authentication for modern web apps is implemented by JWT. With our solutions scaling along with your business, we further provide optimized performance and enhanced app security for single-page apps or complex microservice environments.
- Full-Stack Authentication Solutions – AQe Digital provides full-stack authentication solutions with OAuth 2.0, JWT, MFA, and RBAC. We enforce secure and seamless user management on web and mobile platforms to fulfill the needs of your business.
- Token Refresh & Revocation Strategies – We design a robust token refresh and revocation strategy to protect your data. At AQe Digital, we keep your user sessions seamless while ensuring that your data is secure by either token revocation or token refresh.
- Single Sign-On Implementation – AQe Digital focuses on the development of various Single Sign-On (SSO) solutions, which allow users to access more than one application after authenticating themselves once. Our SSO implementations are easy to use and secure, ensuring a very great user experience when across platforms and avoiding logins.
- OAuth 2.0 and JWT App Security Audits and Consulting – The audits identify vulnerabilities in the OAuth and JWT processes to bolster your app security from end to end. Our consulting services ensure your implementation aligns with the latest best practices.
- Cross-Framework OAuth & JWT Expertise – AQe Digital, your digital transformation partner, brings cross-technology expertise to integrate OAuth and JWT seamlessly across your stack, be it React or Node.js, Spring Boot, or something else so that you have flexibility with app security.